The NetBuster - Busting the Net For You
A WiFi access point that automatically keeps all of your connected devices encrypted and anonymous at all times!
Get Involved! Join our discord chat community here and lets talk how to make the most secure OpenSource router in the world.

What is it?
The NetBuster is a device that connects to any public or private internet connection via WiFi or Ethernet. Connection to the internet is selected from the NetBuster's internal webpage. Once connected it encrypts the connection through the Tor network or a private VPN. Once that is complete all of your personal devices can safely use the internet anonymously and encrypted.
Why use a NetBuster?
* Public WiFi hotspots are not encrypted, hackers can monitor your traffic. NetBuster protects your traffic.
* Internet websites track you through the following ways:
- IP Address: They can tell where you are coming from.
- HTTP Referrer: They can find what site or search engine referred you to them.
- Cookies: They store information in your browser for tracking to hand to them next time and other sites.
- User Agent: Your Browser tells the website what OS you have, your brower type, plugins, and version.
- NetBuster blocks all of this and makes you anonymous on the internet.
* Public WiFi access points in hotels, airplanes, or boats have a limit of the number of devices allowed. Netbuster lets you have unlimited devices on any internet connection. It acts as a personal router for you.
* No personal device needs to install ANY software. The Netbuster does all the work for you, just connect to it and go knowing your protected.
* Using anonymous networks like TOR can be scary to install on your personal equipment. Netbuster isolates your devices connecting to these networks by having TOR run internally on NetBuster. Turn off NetBuster and you are cleanly cut-off from all those networks.
* Senate votes to allow FBI to look at your Web Browsing History without a Warrant
* ISP's are now monitoring everything you do on the internet without your permission.
* The box is device made of all off-the-shelf components for anyone to buy for around $65.
* The software is 100% open source.
* VPN's that claim to be safe anonymous and secure can be bad and actually sell your data behind your back:
Hotspot Shield Sells your Data to 3rd Parties.
How it works
1) Turn on the NetBuster.
2) Point your wifi device and connect to the SSID: netbuster.io
3) Login to the Netbuster webpage (192.168.42.1)
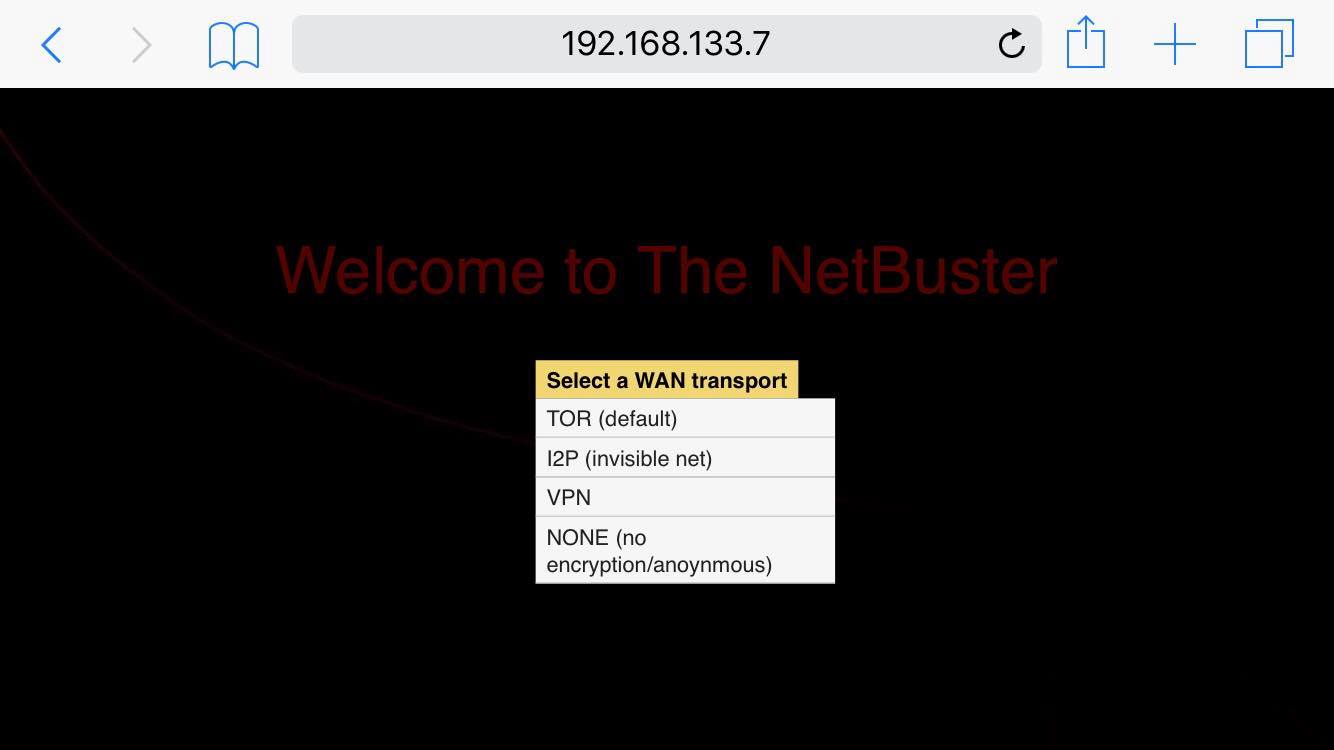
4) Select which WAN transport you want to use (default: TOR)
5) Select an outbound WiFi internet connection you want to go through (e.g. Starbucks)
Then the NetBuster connects to it and routes you automatically through the TOR network or whatever transport you selected which is encrypted and anonymous. Unless you picked no transport which is for maximum performance.


Features
* Unlimited devices can share one internet connection.
* Selection of BackEnd transpots: TOR (TOR Onion Network), I2P (Invisible Internet).
* Portable encryption and anonymous traffic using backend transports.
* Easy to use web GUI to select which internet connection to use.
* Isolation of anonymous networks from your critical systems.
How do I build a NetBuster?
Here is the HW component list:
* CanaKit Raspberry Pi 4 4GB with Clear Case and 3.5A Power Supply - $82.99
* USB Edimax AC1200 Wireless 866Mbps 802.11n adapter - $21.24
* SanDisk 32GB Micro SD card - $9.77
* Anker Powerline Micro USB 4 inch cable (2pk) - $8.99
* Anker 10,000mAh External Battery PowerCore - $19.99
Where do I get the software from?
* NetBuster GitHub
Where can I talk to the developers and community?
* NetBuster Discord Chat
What does a NetBuster look like?
NetBuster Hardware with keyboard, mouse, and monitor all connected


What does a portable NetBuster on battery look like?
NetBuster running a Anker battery. Prelim battery testing shows:
Anker droped 25% of total battery for full day of NetBuster idle with light web traffic.

How much is encrypted and anonymous?
Encryption is only from the Netbuster to the Tor exit node or the VPN company. After that traffic is no longer encrypted to the final destination location, nor can it be. However running SSL(secure web pages) will allow encryption end-to-end and it is suggested you always run SSL if possible.
There are always new ways people try to collect data from you so nothing is 100% anonymous. For example cookies are difficult to block as lists of known sites you want to block are updated often but never fully complete.
Just be aware you are never 100% encrypted on all streams and apps end-to-end, nor are you 100% anonymous however NetBuster tries to get you as close to 100% as possible.
Is NetBuster 100% Complete and done?
No. It is a work in progress. Some features are not complete and new features are constantly being thought of to be added.
Did anything influence NetBuster?
Yes. The Trace Buster Buster!









